Organizations rely on the security that cyber insurance offers as the frequency and severity of cyberattacks rise. In the event of a successful breach or ransomware attack, the appropriate policy will minimize responsibility and keep damages in check.
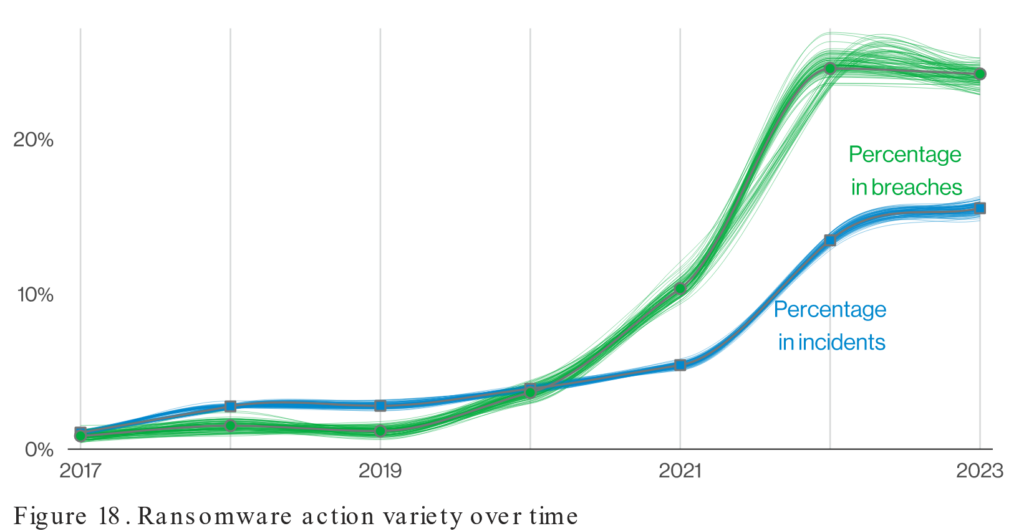
Until recently, it was common to have few if any technical requirements for cyber insurance. According to a longitudinal study conducted by Verizon, the percentage of breaches has skyrocketed over the last 2 years. This escalation has forced insurance companies to fundamentally change the requirements for getting or renewing cyber insurance. Organizations must now show they can defend against ransomware assaults using a variety of security solutions.
Source: DBIR Report 2023 – Results and Analysis – Intro | Verizon Business
The ability to enforce multifactor authentication (MFA) across internal and external resources within the environment, as well as the monitoring and protection of all privileged accounts, are just a few examples of the specific identity security measures that underwriters now demand to be in place. These measures are intended to stop threat actors from using lateral movement to spread ransomware within the targeted environment. The difficulty in this situation is that many organizations don’t currently have the appropriate protections in place to satisfy these requirements.
Threat actors are becoming more adept at using lateral movement to successfully spread payloads throughout an entire environment at once as the number of ransomware assaults increases (71% higher in the last year) because of the billions of stolen credentials that are now available on the dark web. Blind spots in identity protection have recently led to high-profile attacks on major corporations such as Apple, Accenture, Nvidia, Uber, Toyota, and Colonial Pipeline. For this reason, underwriters have instituted strict requirements that businesses must achieve to qualify for a policy. Many organizations have been caught off guard by the renewal requirements and are having difficulty grasping the technical complexities as well as identifying the best solutions to meet the requirements for a policy. Luckily, there is a solution that allows organizations to handle even the most difficult requirements using a simple framework.
Framework:
Different insurance providers will have slightly different technical requirements, but in general, these are the 6 main requirements that we run into:
Multi-Factor Authentication (MFA)
1. Multifactor Authentication (MFA) – This form of authentication simply means that there will be more than one piece of information required before allowing a user access to resources. Generally this will be something that you know (a password) and something that you have (like an app on your phone that generates rotating codes). If you know the password but don’t have the app on your phone, you will be denied access. See this blog post for more information on MFA – How to Prevent 99.9% of All Identity Hacks – Philantech3 (ptech3.com)
Email Filtering / SPAM Filtering
2. Email Filtering / SPAM Filtering – This is a service that automatically checks incoming email to filter out email with malicious links.
Endpoint Detection Response (EDR) and Next Generation Antivirus (NGAV)
3. Endpoint Detection and Response (EDR), sometimes known as Endpoint Detection and Threat Response (EDTR), is an endpoint security solution that continuously scans end-user devices for malware and ransomware to identify them and take appropriate action. Next-gen antivirus employs advanced monitoring to seek out threats of all kinds. NGAV protects against previously unheard-of threats. In other words, NGAV doesn’t wait to start working until a network security danger has been identified. It is always on guard.
Offsite, Segregated, and Immutable backups
4. This is a complicated way of saying that your backups need to be air-gapped or separated from your daily work environment. In other words, you need to prove that your backups are stored in such a way that a network compromise of your working file system does not have the ability to traverse to your backup set. Yes, this requirement extends to your cloud environments like Microsoft 365.
Vulnerability Management
5. This includes the requirement that all critical vulnerabilities are patched within 30 days.
Cyber Security Awareness Training and Phishing simulation
6. The organization needs to prove that their employees and volunteers receive regular and ongoing security awareness training and regular simulated phishing attacks. Phishing attack simulations are email campaigns designed to simulate a threat actors attempts to extract sensitive information from your employees. With this policy in place, an organization can measure which employees are fooled by the simulation and give up sensitive information. This can be used for targeted training.
At Philantech3, we are passionate about helping organizations avoid disruptions. We’ve developed a comprehensive support system that allows organizations to focus on their primary objectives without getting distracted by cyber security concerns. Reach out today for more information.
Information Technology Aligned With Your Business Goals?
Philantech3 is a complete IT services & IT support company working with organizations in Spokane.

With an undergraduate degree in Applied Management, a graduate degree in Business Administration and as a doctoral candidate in Organizational Psychology, let’s just say that business and leadership are Wil’s passions! He is also a small business owner who understands the rigors and joys of business building.

Recent Comments